How to create PCAP-NG files
As described on the Wireshark Q&A site you can dump the network traffic on a Mac easily to a PCAP-NG file:
sudo tcpdump -q -n -i pktap,en0 -k -w mytrace.pcapng
The file format of this dump, PCAP-NG (PCAP Next Generation Dump File Format) contains a lot more information than the old PCAP format used by Wireshark.
If you want to go straight to the file format specification of PCAP-NG, click here.
Now if you want to see all the details of such a file outside Wireshark, an almost complete grammar for Synalyze It! (macOS) and Hexinator (Linux and Windows) was built. You can download the grammar from the Synalyze It! web site or directly from the applications.
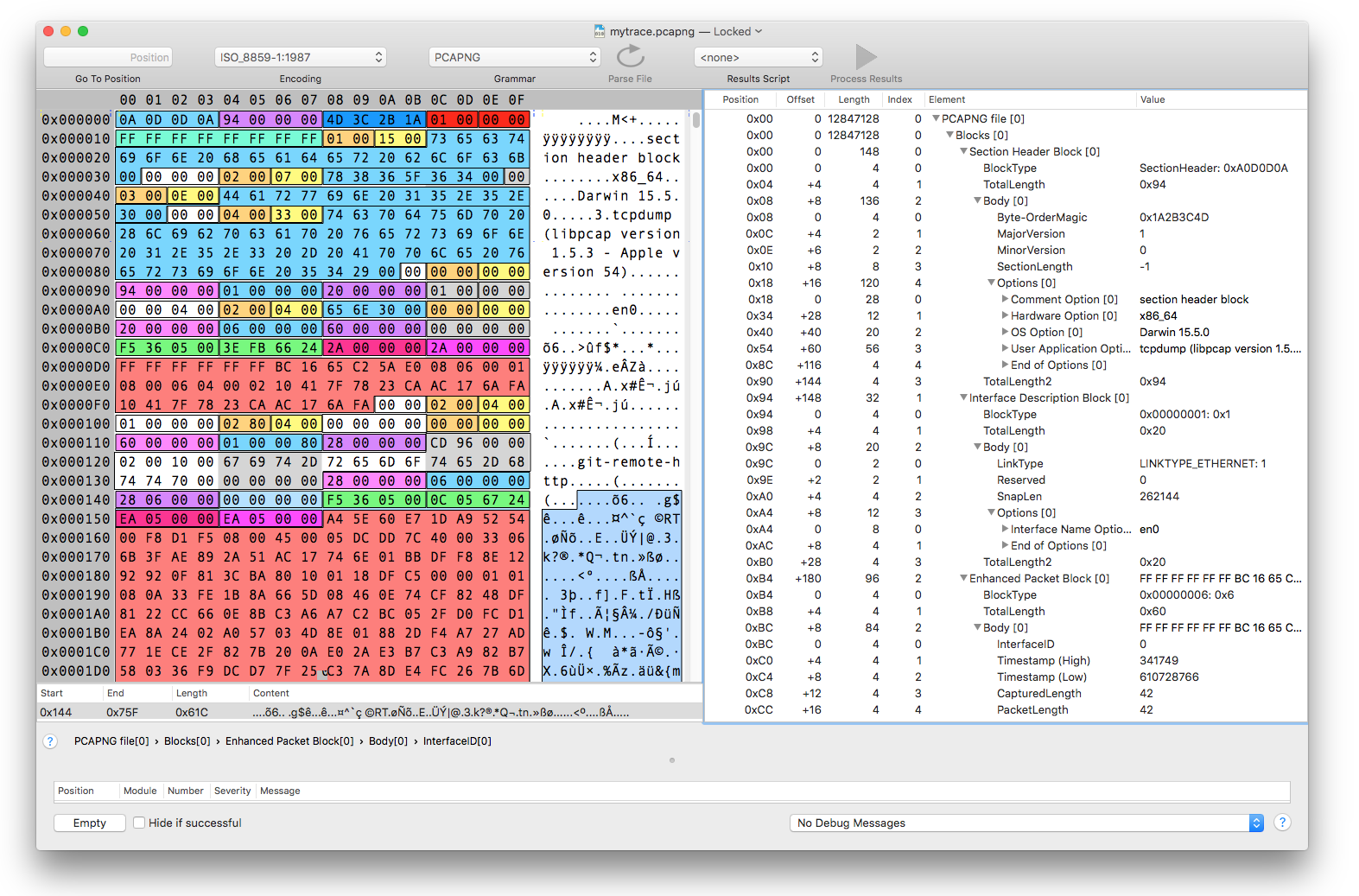
Decoded PCAP-NG file
Structure of a PCAP-NG file
Blocks
The whole file consists of a sequence of blocks of different types. Each block starts with a 4-byte block type, followed by a 4-byte block length (repeated at end of block). Between the block lengths is the actual block content (body) located.
The Section Interface Block and Interface Description Block have to be present in a file at least once, all others are optional. The actual data can be found in the Enhanced Packet Block and Simple Network Block.
While the blocks are not nested there’s still a hierarchy: all blocks following a section header block belong to the same section. Likewise all simple and enhanced packets as well as the interface statistics belong to the preceding Interface Description Block.
Options
Each block can embed optional fields. All these fields conform to a common format. Similar to blocks an option field starts with an identifier (code) and the field length, both two bytes long. This allows the reading software to skip unknown options easily.
Endianness
The file format allows numbers stored in little or big endian.